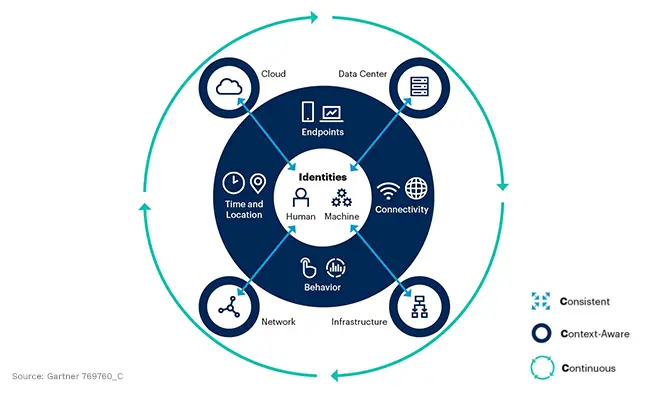
The cybersecurity landscape has embraced a pivotal aphorism: "identity is the new perimeter." This paradigm shift signifies a move away from relying on corporate firewalls as the primary defense against external threats, towards prioritizing user identity to inform access control decisions.
This evolution reflects the transition to security architectures founded on the zero trust principle, which dictates that mere proximity between entities cannot be the basis for trust. This change is particularly relevant in today's era of hybrid cloud networks, where traditional firewall boundaries are no longer adequate.
The Advent of Next-Generation IAM
The challenge of securing modern, distributed IT environments has given rise to the development of next-generation identity and access management (NG-IAM) systems. These systems are designed to be agile, capable of navigating the complex landscape of cloud services, SaaS, and on-premise solutions that typify enterprise networks. A key component of these NG-IAM systems is their emphasis on identity hygiene—ensuring that user permissions and entitlements are meticulously managed, audited, and cleansed to prevent security vulnerabilities caused by misconfigurations or inappropriate settings.
Spotlight on Identity Hygiene
The concept of identity hygiene has been championed by cybersecurity experts like SPHERE, underscoring the importance of diligent management of user permissions to secure the virtual perimeter of enterprises. Proper identity hygiene is imperative for maintaining the integrity of the hybrid security perimeter, satisfying the stringent requirements of modern control auditors and compliance assessors. The meticulous management of permissions and identities is therefore not just a compliance requisite but a foundational element of effective cybersecurity strategy.
Embracing Identity as the Security Linchpin
In the realm of hybrid cloud networks—which is fast becoming the standard—embracing the notion that "identity is the new perimeter" is essential. Ensuring the efficacy of this newly defined perimeter necessitates a dedicated commitment to comprehensive identity hygiene programs. SPHERE's platform exemplifies the implementation of this concept, setting a benchmark for identity-based access control in the enterprise.
This shift towards identity-centric security models heralds a new era in cybersecurity, emphasizing the need for robust identity hygiene practices to safeguard against evolving threats.
We're keen to hear your insights and engage in further discussion on the transformative role of identity in cybersecurity.